Regulatory Compliance Overview
Industrial control environments can’t afford gaps in cybersecurity. New laws and standards now require operators to prove that they’ve implemented robust risk-management processes, threat detection and governance frameworks.
Our Regulatory Compliance offering begins with a tailored gap assessment that benchmarks your current controls against every applicable requirement. We then provide a clear remediation roadmap—and stick with you through implementation to full audit-readiness.
No two facilities are identical, so we adapt to your exact mix of standards—whether that’s NIST CSF, NERC-CIP, NIS2, IEC 62443 or local regulations—and align every control to your business context.

Why Conduct a Gap Assessment?
A compliance gap assessment gives you an objective snapshot of where your cybersecurity measures meet—or miss—the mark. We conduct in-depth discovery sessions, review your policies, inspect your network architecture and test your perimeter controls.
For each requirement, we rate your existing controls and highlight any shortfalls. Then, we prioritise our recommendations based on risk reduction, cost and complexity—so you tackle the highest-impact fixes first, whether that’s quick wins or major upgrades.
Key Benefits
- Get a definitive baseline of your OT controls against live regulations
- Detect critical non-compliances before auditors do
- Focus your budget on the fixes that deliver the biggest risk drop
- Arm executives with polished reports and dashboards
- Simplify future audits with organised evidence and checklists
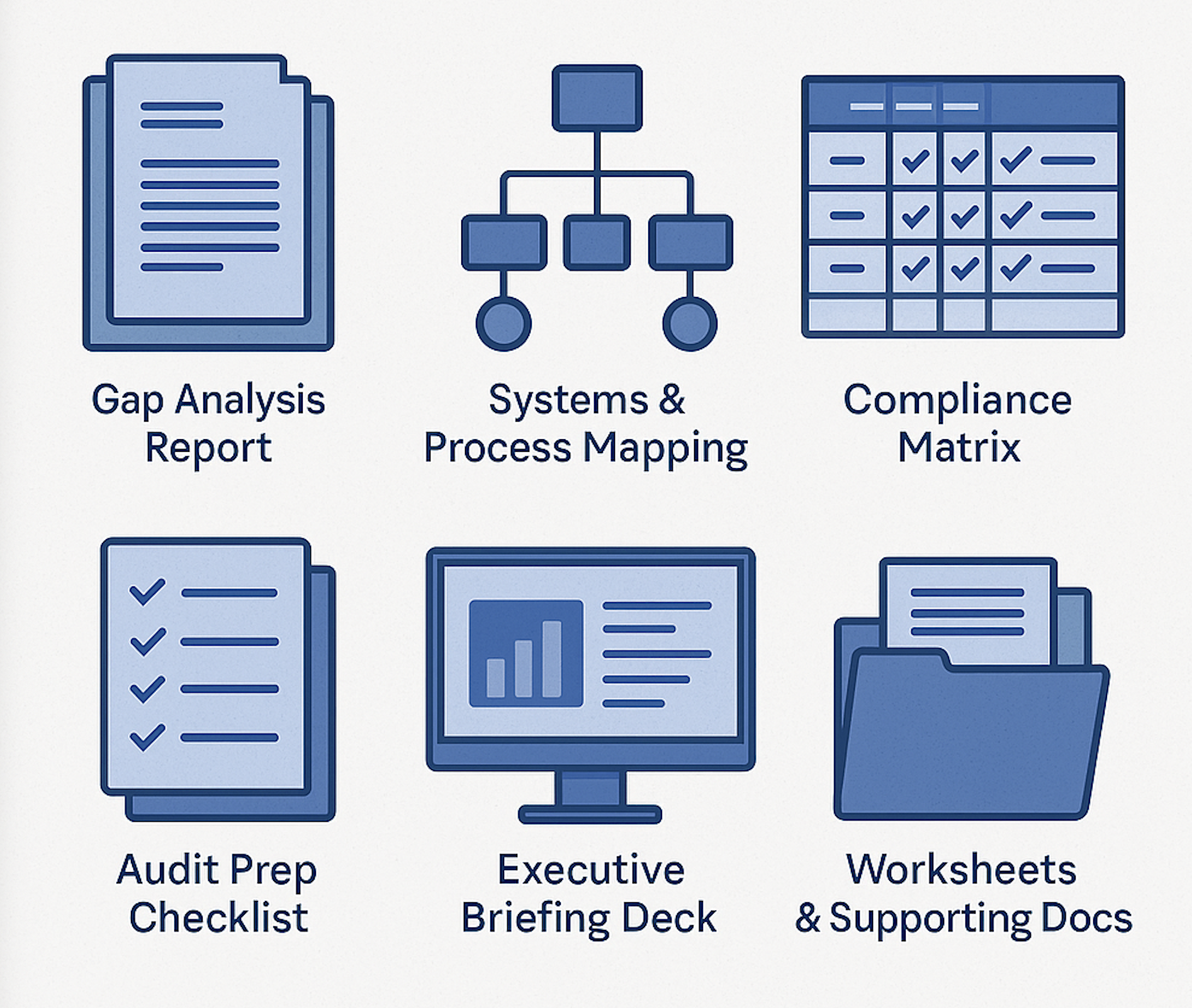
What You’ll Get
- Gap Analysis Report: Detailed As-Is vs. To-Be findings
- Systems & Process Mapping: Visual asset-to-control diagrams
- Compliance Matrix: Clause-by-clause pass/fail chart
- Audit Prep Checklist: Step-by-step itemisation for inspectors
- Executive Briefing Deck: High-level summary for stakeholders
- Worksheets & Supporting Docs: Raw data, policies & templates
Global Regulatory Landscape
United States (NIST CSF, NERC-CIP)
The DHS enforces risk-management frameworks; NERC-CIP is mandatory for all registered energy entities.
European Union (NIS2)
Member states must enforce minimum security measures by September 30, 2024, with cross-border cooperation on incidents.
United Kingdom (CPNI & OG86)
CPNI issues guidance; HSE’s OG86 directs inspector audits at high-hazard and COMAH sites.
Australia (ACSC)
The ACSC publishes best practices and supports incident response for critical infrastructure.
Saudi Arabia (NCA)
The National Cybersecurity Authority sets national policies and assists local operators.
Qatar (NCC)
The National Cybersecurity Committee defines standards and oversees critical infrastructure security.
UAE (NESA)
NESA issues regulations and provides guidance to safeguard the UAE’s strategic sectors.
Purdue Model & Compliance
We leverage the Purdue Model to segment your OT architecture into clear zones and conduits—then map each layer’s controls to your chosen standards, ensuring you can demonstrate compliance at every network level.